Have you ever stopped to think about whether someone else is accessing your iPhone remotely?
With the amount of personal information and data stored on our phones, it’s important to be aware of any potential security breaches.
The thought of someone else accessing your phone without your knowledge is frightening, but there are ways to detect if this is happening.
In this article, we’ll explore how to tell if someone is accessing your iPhone remotely and what steps you can take to protect yourself.
The signs that someone may be accessing your iPhone remotely include faster-than-usual battery drainage, unexpected Face ID or Touch ID setup, unfamiliar apps or profiles, and a recording indicator when not using the camera or microphone.
These signs indicate that someone may have gained access to your device without your knowledge, and you should investigate further to confirm whether this is the case.
What Does Remotely Accessing an iPhone Mean?
Remotely accessing an iPhone means that a person can control an iPhone from a remote location without physically having access to the device.
This is done by using specialized software that allows access to the iPhone’s features such as the camera, microphone, messages, and contacts.
This type of access can be done through wireless networks or the internet, making it easier for intruders to gain access to the iPhone.
Why does Someone do this?
There are several reasons why someone might remotely access an iPhone. Some individuals may do this for legitimate reasons, such as parents who want to monitor their children’s online activities or employers who want to keep tabs on their employees.
However, in most cases, remotely accessing an iPhone is done for malicious reasons. Cybercriminals can use this method to gain access to sensitive data, such as bank account details, personal information, and intellectual property.
Is Someone Sneaking into Your iPhone? Here’s How to Find Out!
Your iPhone is more than just a device that stores your contacts, messages, and photos. It is a gateway to your personal life, containing sensitive information that could harm you if it falls into the wrong hands.
That’s why it’s important to stay vigilant and know how to detect any unauthorized access to your device. There are a few telltale signs that can help you figure out if your phone is being remotely accessed.
Monitor unusual Apps
Hackers can remotely access your iPhone by installing spyware or malware apps that can collect data, track your location, record calls, and activate your camera or microphone.
Take Action
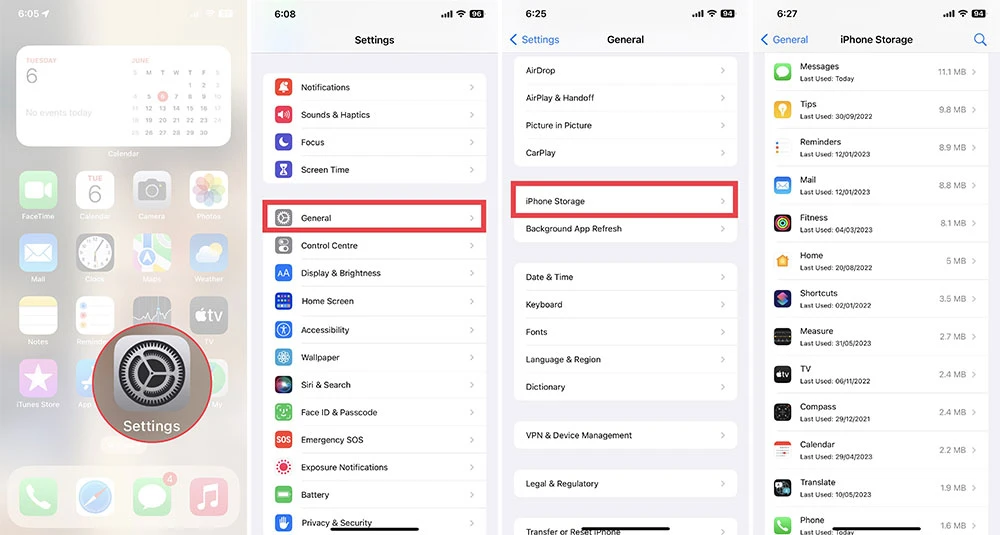
To check for unusual apps, go to Settings > General > iPhone Storage and delete any suspicious apps or those with negative feedback from the App Store.
Pop-Ups Warning
Pop-ups warning about a virus or software update on your iPhone may indicate remote access attempts. Such pop-ups are usually fake and designed to trick you into downloading malicious software or giving away your personal information.
Take Action
Do not click on them, instead clear your browser cache and cookies by going to Settings > Safari > Clear History and Website Data.
Battery Draining Fast
Faster-than-usual battery drainage on your iPhone may indicate remote access, as remote access apps can consume battery power by running in the background.
Take Action
To check for abnormal battery usage, go to Settings > Battery and check for any apps that are using a lot of power. If you notice this, consider deleting the apps or restoring your iPhone to its factory settings.
Data usage increased substantially
Unusual spikes in data usage on your iPhone may indicate remote access, as remote access apps can consume a lot of data to send and receive information.
Take Action
To check your data usage, go to Settings > Cellular and look for any apps that are using a lot of data. If you notice any unusual spikes, consider deleting the apps or turning off cellular data for them.
Unrequested Apple ID verification codes
Receiving unrequested Apple ID verification codes may indicate attempted remote access to your iCloud or other Apple services, which could lead to accessing your personal information.
Take Action
Enable two-factor authentication for your Apple ID, change your password, and security questions regularly to prevent unauthorized access.
Unusual Phone Behaviours
Unusual behaviors on your iPhone such as freezing, crashing, restarting, or making noises may indicate remote access. These behaviors could affect your device’s performance and functionality.
Take Action
Try updating your iOS software, resetting your network settings, or restoring your iPhone from a backup to fix the issues. If these solutions do not work, contact Apple Support or visit an Apple store for assistance.
Review Apple ID
Reviewing your Apple ID account and settings is crucial if you suspect remote access to your iPhone. Go to Settings > [your name] > Password & Security > Devices to identify any unfamiliar linked devices or suspicious activity.
Take Action
Also, check your account details, and recent activity, and sign out of any untrusted devices or browsers through appleid.apple.com.
Slow Performance
If your iPhone is running slower than usual it may indicate remote access, as the software can consume your device’s resources.
Take Action
To improve performance, try clearing storage space, closing unused apps, disabling background app refresh, turning off location services, and using Low Power Mode to reduce power consumption and extend battery life.
How to Stop Someone from Accessing Your iPhone Remotely?
If you suspect that someone is accessing your iPhone remotely, you might be worried about your privacy and security. Remote access can allow hackers to steal your personal information, spy on your activities, or even take control of your device.
Luckily, there are plenty of ways you can stop someone from remotely accessing your iPhone. Here are some steps you can take to protect your phone and your data.
Update Your iPhone Software
Apple regularly releases updates for iOS that fix bugs and improve security features. These updates can prevent hackers from exploiting vulnerabilities in the system and gaining access to your phone.
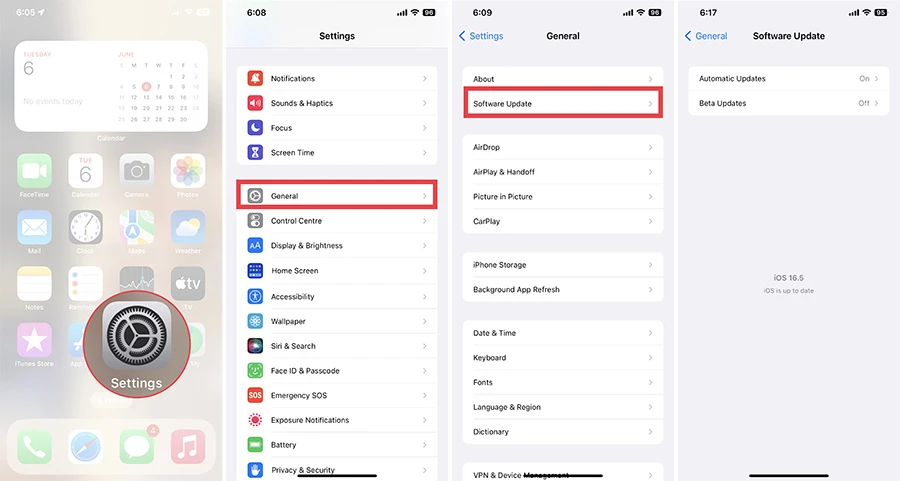
To update your iPhone software, go to Settings > General > Software Update and tap Download and Install if there is a new version available. You can also enable automatic updates by toggling on the option under Software Update.
By using the latest iOS version, you can benefit from the latest Apple security updates and protect your phone from remote access.
Enable Two-Factor Authentication
Two-factor authentication is a security feature that adds a second layer of verification when you sign in to your account or use certain services.
This means that you need to enter not only your password but also a code that is sent to your trusted device or phone number.
To enable two-factor authentication for your Apple ID, go to Settings > [your name] > Password & Security and tap Turn On Two-Factor Authentication. Follow the instructions on the screen to set up a trusted device and a trusted phone number.
By enabling two-factor authentication, you can make it harder for someone to access your account or use services like iCloud, iMessage, FaceTime, or App Store without your permission.
Activate “Find My iPhone”
“Find My iPhone” is a feature that allows you to locate, lock, or erase your lost or stolen device using another device or a web browser.
To activate “Find My iPhone” on your device, go to Settings > [your name] > Find My > Find My iPhone and toggle on the option. You can also enable other options like Send Last Location or Share My Location if you want.
By activating “Find My iPhone”, you can use the following features if someone tries to access your phone remotely:
- Locate: You can use another device or a web browser to sign in to iCloud.com/find or use the Find My app to see the location of your device on a map.
- Lock: You can use another device or a web browser to lock your device with a passcode and display a custom message on the screen.
- Erase: You can use another device or a web browser to erase all the data on your device and restore it to factory settings.
These features can help you prevent someone from accessing your data or using your phone if it is lost or stolen.
Use a Strong Password
A strong password is one that is unique and difficult to guess by others. It should be at least eight characters long and include a combination of letters, numbers, symbols, and uppercase and lowercase characters.
To change the password for your device, go to Settings > Face ID & Passcode (or Touch ID & Passcode) and tap Change Passcode. Enter your current passcode and then enter a new one.
To change the password for your Apple ID, go to Settings > [your name] > Password & Security and tap Change Password. Enter your current password and then enter a new one.
By using a strong password, you can make it harder for someone to unlock your device or access your accounts without your knowledge.
Monitor iCloud Activity
iCloud is a service that allows you to store and sync your data across different devices. However, it can also be used by someone to access your data or spy on your activity if they have your Apple ID and password.
To monitor your iCloud activity, go to Settings > [your name] and tap iCloud. Here you can see how much storage you are using and what apps are using iCloud. You can also manage your iCloud backups and turn off the apps that you don’t want to sync with iCloud.
To monitor your devices that are signed in with your Apple ID, go to Settings > [your name] and tap Devices. Here you can see the list of devices that are using your Apple ID.
You can tap on each device to see more details like the model, the OS version, the serial number, and the last location. You can also remove any device that you don’t recognize or don’t use anymore by tapping Remove from Account.
Use Anti-Virus Software
Anti-virus software can help you detect and remove any malware that might be installed on your phone by hackers. Malware can allow someone to access your phone’s camera, microphone, screen, and files without your knowledge. To use anti-virus software on your iPhone, you need to:
- Install a reputable anti-virus app from the App Store, such as Norton, McAfee, or Avast.
- Scan your phone regularly for malware using the app. You can also schedule automatic scans for convenience.
- Set up virus alerts on your phone so that you get notified if any malware is detected.
Disable Unnecessary Features
Disable some features that might be exploited by hackers. These include Siri and other voice commands, Bluetooth and Wi-Fi, and location services for apps.
These features can allow someone to control your phone or track your location without your consent. To disable these features on your iPhone, you need to:
- Disable Siri and other voice commands by going to Settings > Siri & Search and turning off Listen for “Hey Siri“, Press Side Button for Siri, and Allow Siri When Locked.
- Turn off Bluetooth and Wi-Fi when not in use by swiping down from the top right corner of your screen and tapping on the Bluetooth and Wi-Fi icons.
- Turn off location services for apps by going to Settings > Privacy > Location Services and toggling off the apps that don’t need your location.
Monitor Your Phone Activity
Monitor your phone activity for any signs of intrusion. This can help you identify and stop any unauthorized access before it causes any damage. Some of the things you should look out for are:
- Check your phone for unusual activity, such as battery drain, overheating, slow performance, or increased data usage.
- Look for suspicious file downloads, such as unknown apps or documents that you didn’t download yourself.
- Keep an eye out for any strange notifications, such as pop-ups, messages, or calls from unknown numbers or contacts.
Manage Your App Permissions
Manage your app permissions carefully. This can help you limit what apps can do on your phone and prevent them from accessing sensitive information or functions. Some of the things you should do are:
- Check which apps have access to your phone by going to Settings > Privacy and tapping on each category, such as Camera, Microphone, Photos, etc.
- Remove any apps that you don’t recognize or trust by tapping and holding on the app icon and selecting Delete App.
- Revoke any unnecessary permissions by toggling off the apps that don’t need them.
By following these tips, you can stop someone from accessing your iPhone remotely and keep your phone safe and secure.
Conclusion
It’s important to be aware of the possibility of remote access to your iPhone. Don’t ignore any suspicious activity, such as sudden battery drain or unusual app behavior. Take action if you suspect your device has been hacked by following the steps we’ve outlined.
Stay informed about the latest security threats to protect your personal information. By being proactive, you can keep your iPhone and your data safe. Remember, prevention is always better than cure, so take the necessary steps to secure your iPhone today.

